Let’s start with the basics. A zero-day exploit refers to a security flaw in software, hardware, or firmware that is unknown to the vendor. This makes it a prime target for attackers. Think of it like a secret backdoor to a house—until the homeowner discovers it, anyone can sneak in without being noticed.
Hackers exploit these vulnerabilities before the software developers can fix them, which is why these attacks are so dangerous. Since there's no immediate patch or solution, the impact of these exploits can be devastating. For instance, an attacker could steal sensitive data, disrupt services, or even take control of entire systems
Zero-day exploits are dangerous for three main reasons:
Stuxnet Worm (2010) - Stuxnet was a sophisticated zero-day exploit used to disrupt Iran's nuclear program. It targeted industrial control systems, demonstrating how such attacks could have geopolitical consequences.
Google Chrome Exploit (2023) - In 2023, a zero-day vulnerability in Google Chrome allowed attackers to execute arbitrary code. It highlighted how even widely trusted software isn’t immune to such threats.
Sony Pictures Hack (2014) - Cyber attackers used a zero-day exploit to leak sensitive company data.
Zoom Security Breach (2020) - Disclosed vulnerabilities in the video conferencing software, which allowed unauthorized access.
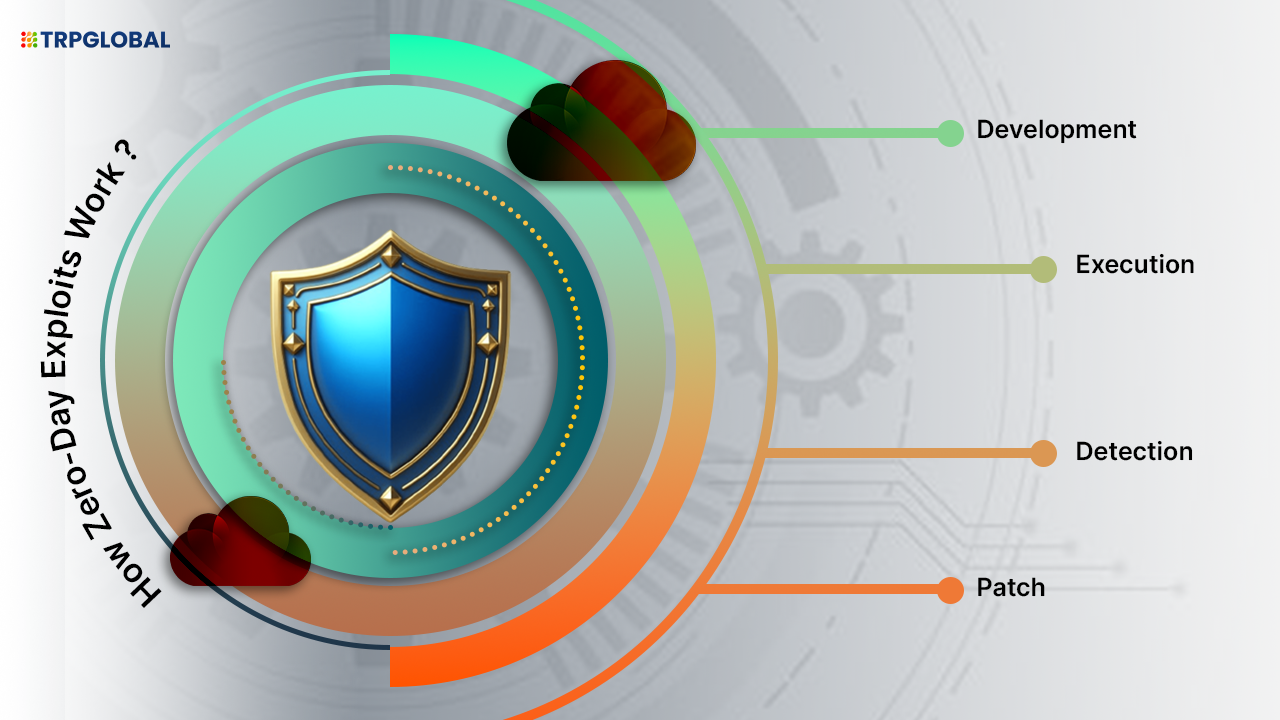
Here’s a step-by-step breakdown of how a zero-day exploit typically unfolds developers.
Zero-day exploits don’t discriminate—they can target:
While zero-day attacks are challenging to prevent entirely, there are steps to minimize the risks:
1. Monitor Reported Vulnerabilities
2. Implement Layered Security
3. Automate Regular Updates
4. Adopt Next-Gen Antivirus Solutions
5. Employee Training and Awareness
6. Deploy Advanced Threat Intelligence
7. Backup Critical Data
By initiating these methods into your cybersecurity strategy, you create a strong defense against zero-day exploits.
As technology evolves, so do cyber threats. Machine learning and AI are being leveraged by both attackers and defenders. For instance, AI can help identify vulnerabilities faster, but it can also be used by hackers to automate exploit creation.
Understanding What is a zero-day exploit and recognizing Zero-day attack examples is the first step toward better cybersecurity. At TRPGlOBAL, we specialize in protecting businesses from emerging threats.
Want to stay ahead of cyber risks? Visit our Contact Us page and let’s secure your digital future together!
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.