If you’ve ever sat in an audit review for your ERP system and heard the dreaded words “Segregation of Duties violation,” you know how quickly the room tenses up.
Segregation of Duties (SoD) is a cornerstone of internal controls in ERP systems like SAP, Oracle Fusion Cloud, Workday, and Microsoft Dynamics. It’s about ensuring that no single individual has enough access to perform and conceal a malicious or simply mistaken transaction.
When SoD conflicts exist, organizations face risks of fraud, compliance violations, audit findings, and even reputational damage. In this blog, we’ll break down the top 7 SoD conflicts every IT and cybersecurity professional should know and more importantly, how to mitigate them with practical, real-world strategies.
Before diving into the conflicts, let’s recap why SoD is non-negotiable:
Think of SoD as your organization’s “checks and balances” system. Without it, you’re leaving the financial keys to the kingdom in the wrong hands.
The risk: An employee who can both create a vendor and process payments could set up a fake supplier and pay themselves.
Example: In one case, an accounts payable clerk in a large manufacturer created ghost vendors and routed payments worth millions.
Mitigation:
The risk: If a user can both create customer orders and issue credit memos, they could manipulate sales and refunds.
Example: A retail ERP audit uncovered that one sales manager issued unauthorized credits to friends’ accounts.
Mitigation:
The risk: A user could add fake employees and then process payroll, funneling funds to ghost accounts.
Example: A healthcare provider discovered “phantom employees” receiving salaries, all tied back to one HR/payroll administrator.
Mitigation:
The risk: Someone with both privileges could manipulate stock records and cover up theft or mismanagement.
Example: In a distribution company, an employee adjusted inventory levels after stealing hardware components.
Mitigation:
The risk: A finance user could create fictitious journal entries and approve them, hiding fraudulent activity.
Example: A finance analyst fabricated journal entries to conceal unauthorized transfers, uncovered only during an external audit.
Mitigation:
The risk: An employee could create fake assets and later “dispose” of them, writing off value while pocketing proceeds.
Example: A global bank discovered IT equipment listed as disposed when, in reality, it had been sold off by an insider.
Mitigation:
The risk: A user could create fraudulent POs and confirm receipt of goods never delivered.
Example: In an ERP fraud case, an operations manager approved fake POs and recorded receipt of goods, triggering payments to fraudulent suppliers.
Mitigation:
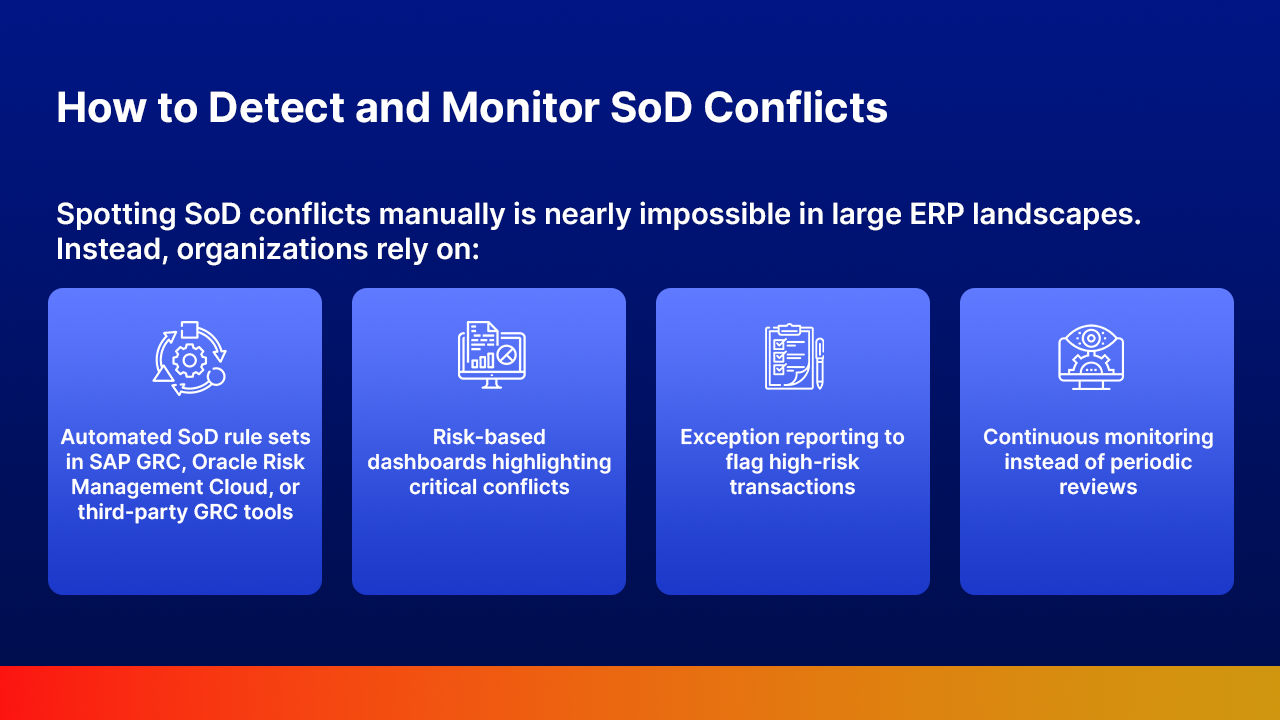
Spotting SoD conflicts manually is nearly impossible in large ERP landscapes. Instead, organizations rely on:
Automation ensures scalability whether you manage 500 or 50,000 users, you can catch conflicts without drowning in spreadsheets.
A global logistics company faced repeated SOX audit findings for SoD violations. Their ERP had 12,000 active users, many with conflicting roles.
By implementing SAP GRC Access Control, they:
Result? Zero audit findings in the next cycle and significant trust gained with both auditors and executives.
To stay ahead of risks, follow these principles:
At TRPGLOBAL, we specialize in helping enterprises identify, remediate, and automate SoD controls across ERP systems like SAP and Oracle. With our RiskSuccess© methodology, we transform access risks into streamlined, audit-ready processes.
By understanding the top 7 conflicts and applying proven mitigation strategies like role redesign, workflow approvals, and continuous monitoring you can dramatically reduce risk.
The key? Don’t rely on manual checks. Invest in automation and governance frameworks like SAP GRC or Oracle Risk Management Cloud to ensure ongoing compliance, stronger controls, and a resilient organization.
Ready to eliminate SoD conflicts and strengthen your ERP security posture? Contact us today to schedule a consultation with our ERP risk experts.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.