Once upon a time, phishing emails were easy to laugh off. Misspelled words, clunky formatting, and outrageous promises ("Click here to claim your $1 million prize!") made them obvious—even to non-technical users.
But today’s phishing scams are different. They’re smart. Subtle. Targeted.
They read like they came from your boss. They reference your actual projects. They show up in your calendar invites or Slack messages.
This is Phishing 3.0, and it’s not just spoofed emails anymore—it’s a full-blown psychological attack, powered by data mining, machine learning, and human error.
To understand where we are, it helps to look back at how phishing has evolved:
Let’s break it down with some real-world scenarios that IT and cybersecurity teams are seeing today:
An employee receives a Slack DM from the "CEO" urgently asking for gift card codes for a client event. The profile picture matches. The writing style feels right. It's a rush.
Reality: The account was created with a similar handle (e.g., ceo_jon.smith) and the attacker scraped previous Slack convos to mimic tone and style.
A calendar invite pops up titled “Policy Review – Action Required.” It includes a Google Drive link to an updated company handbook.
Reality: The invite came from a spoofed domain that looked identical to the internal HR address. The link triggered a credential harvesting site.
A finance team lead receives a voicemail from the CFO, instructing them to approve a wire transfer. The voice is convincing, clear, and mentions an internal project.
Reality: It was a deepfake voice attack created using 30 seconds of publicly available audio from a webinar.
Phishing 3.0 doesn't just trick your eyes—it targets your brain. Here's why it works:
Phishing 3.0 requires Phishing Defense 3.0. Here’s how to level up your organization's strategy:
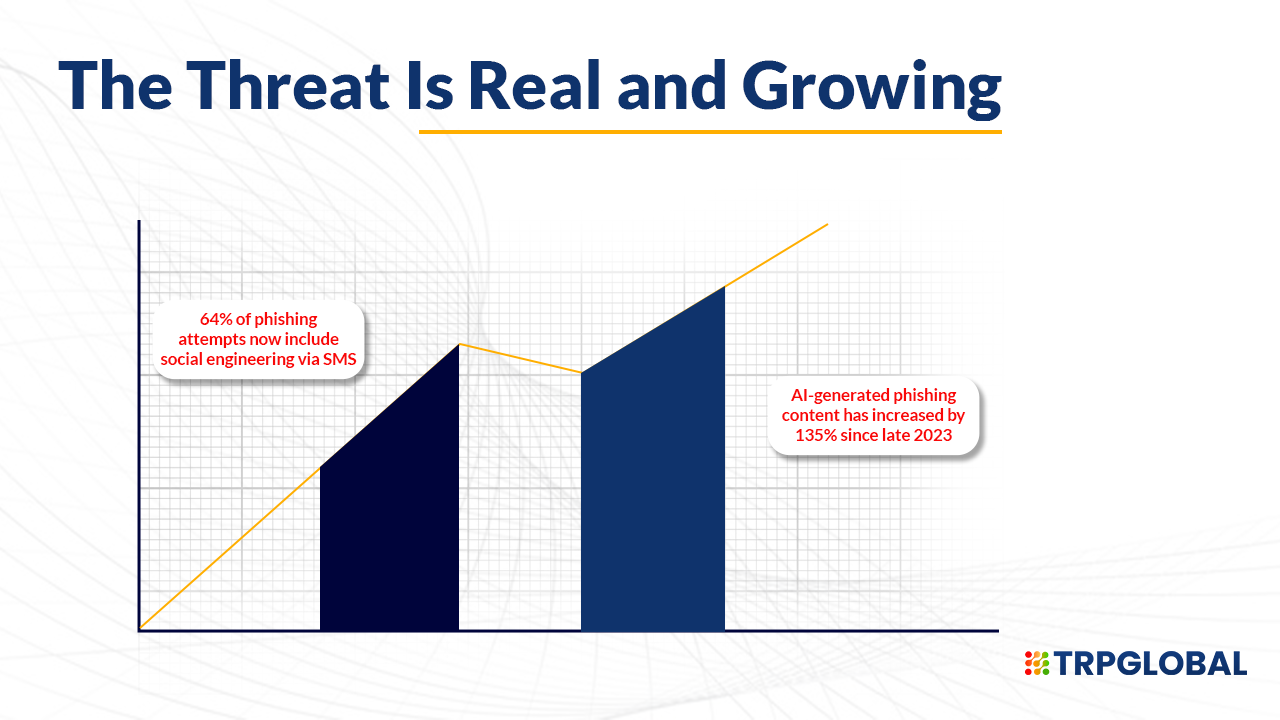
Still think phishing is a low-level threat? The data says otherwise. According to Verizon’s 2024 Data Breach Investigations Report, 36% of all data breaches involved phishing—and that number has been steadily rising year over year. What’s more alarming is that 83% of organizations reported at least one phishing attack in the past 12 months, based on Proofpoint’s 2024 State of the Phish report.
And it’s not just email anymore:
These numbers make one thing crystal clear: Phishing isn’t going away. It’s adapting—and fast.
It’s not just about data loss or financial fraud. A single successful phishing attack can:
Reputation damage from a phishing incident can take years to repair.
The hardest part about Phishing 3.0? It doesn’t look like phishing.
The language is clean. The branding is perfect. The urgency feels authentic. And by the time you realize it wasn’t real… it’s already too late.
As cyber attackers evolve, so must our defenses. IT and security teams can’t rely on outdated assumptions or checkbox compliance. It’s time to train smarter, think deeper, and defend faster.
Concerned about how your team would hold up against a Phishing 3.0 attack? Contact us for a security readiness assessment, awareness training, or a free consultation with our experts. Let’s make sure your next click is a safe one.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.