You passed the audit. The reports are clean. The dashboards are green. But you still feel exposed and you should.
Because here’s the uncomfortable truth: compliance doesn’t equal protection. It never has. In fact, many organizations that suffer breaches were technically “compliant” at the time. What they weren’t was secure. They mistook certification for resilience. They prioritized paperwork over real-world defense.
This blog explores the hidden trap that security leaders fall into when they confuse audit success with actual protection and how to close the gap before attackers find it first.
On the surface, compliance is comforting. It gives stakeholders something measurable—SOC 2, ISO 27001, HIPAA, PCI-DSS. It tells clients: “We take security seriously.” It tells boards: “We’ve done our job.”
But what compliance really means is that you met a set of requirements at a specific point in time.
Security doesn’t work like that. Threats evolve every day. Environments drift. Attackers adapt. If your defenses are designed to pass a test not block an adversary you’re living in a false sense of safety.
Take Capital One’s 2019 breach. They were PCI-DSS compliant, with regular audits and certified cloud usage. Yet, a single misconfigured AWS permission exposed over 100 million customer records.
Equifax? Passed audits. But failed to patch a known vulnerability.
In both cases, compliance wasn’t the problem it was the overreliance on compliance. These organizations had the right paperwork. What they lacked was continuous visibility, configuration management, and human-layer security.
The compliance trap thrives because it’s easy to measure and report. You can assign a team, define a scope, run an audit, and generate evidence. Security, by contrast, is messy. It involves user behavior, evolving threats, alert fatigue, and tech debt. It's harder to quantify and harder to sell to leadership without hard KPIs.
But what’s easier to track isn’t always what matters most. This is how well-meaning organizations fall behind: they follow the framework, check the boxes, and leave the real risks untouched.
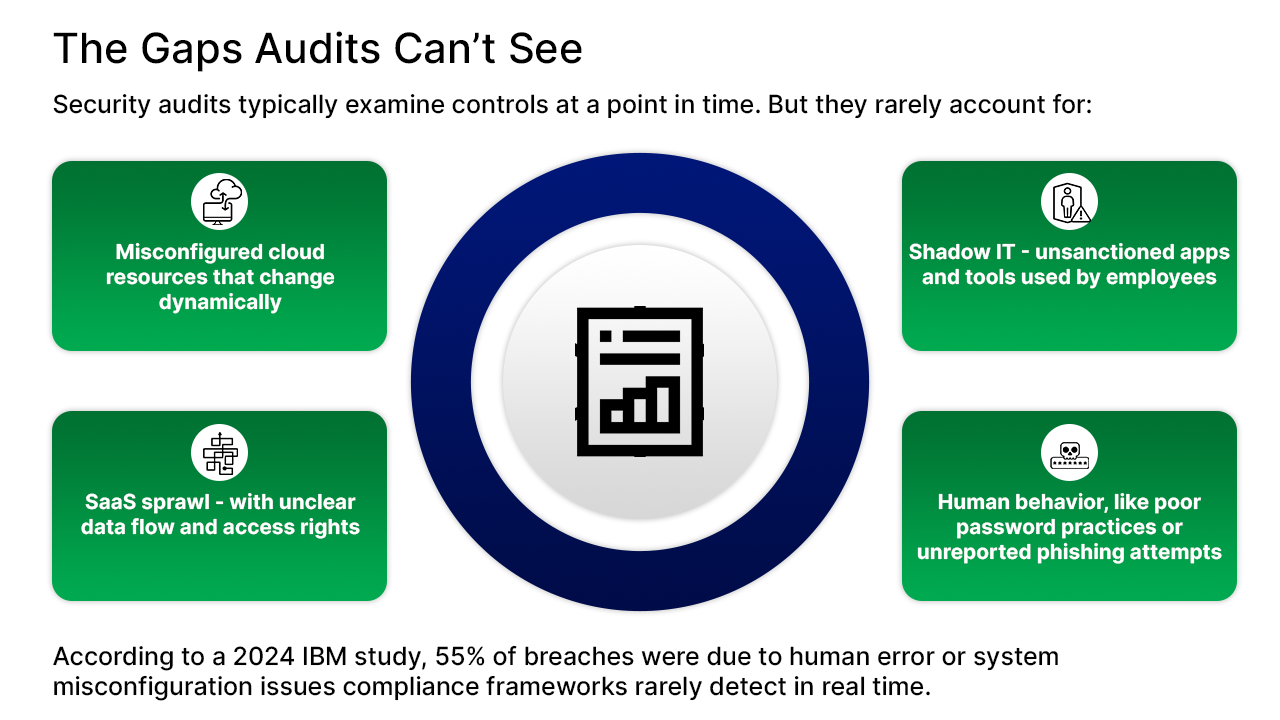
Security audits typically examine controls at a point in time. But they rarely account for:
According to a 2024 IBM study, 55% of breaches were due to human error or system misconfiguration issues compliance frameworks rarely detect in real time.
Most compliance frameworks were written for a different era when threats were slower, systems were on-prem, and visibility was simpler. Today, businesses run on cloud-native apps, remote workforces, and AI-augmented workflows. Yet many audits still focus on static controls like password rotation or physical badge policies. Meanwhile, attackers are exploiting API flaws, abusing OAuth tokens, and hijacking misconfigured Kubernetes pods. The tools have changed. The attackers have changed. But the audits? Not so much. Unless you evolve beyond what the framework requires, you’re protecting a digital environment that no longer exists.
Passing a compliance audit doesn’t test whether your team can spot a phishing email. It doesn’t validate your MFA setup under pressure. It doesn’t simulate how fast you can contain a threat.
Attackers know how to exploit this. They count on organizations being audit-compliant but operationally vulnerable. That’s why breach simulation, red teaming, and behavioral monitoring are far more valuable than checklists.
Compliance might satisfy your auditor. It won’t stop an adversary.
Security maturity starts when compliance becomes a byproduct—not the end goal.
Here’s how leading organizations are shifting to resilience-first security:
These efforts may not show up in your audit report but they dramatically reduce your breach risk.
To regain visibility and true control, smart teams are investing in tools that validate effectiveness, not just existence.
Consider:
The goal? Real-time visibility. Not point-in-time peace of mind.
Still not convinced? Let’s look at the numbers:
The takeaway? The audit stamp doesn't mean you're safe. It just means you're documented.
At the core of every breach is not just a technical flaw it’s a human gap.
A truly secure organization doesn’t just meet frameworks. It builds a culture where:
A security-first culture will naturally pass audits. But a compliance-only culture will always fall short when it matters most.
Compliance is a useful map. It gives you direction. But maps aren’t the territory. Attackers don’t read your audit reports. They look for open ports, misconfigured policies, distracted employees, and outdated software.
True cybersecurity is lived every day, not just reviewed once a year.
If your strategy ends when the audit ends, your risk exposure is just beginning. Make compliance the baseline not the goal. Build resilience. And don’t let checkboxes define your defenses.
Still relying on compliance to gauge your security posture? Let’s go deeper. We help organizations move beyond audit success to real-time security maturity. Contact us today to assess your resilience not just your readiness.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.