As we continue to advance into an era dominated by digital transformation, the concept of Non-Human Identities (NHIs) is becoming increasingly significant in the realm of cybersecurity. NHIs represent a variety of digital entities such as APIs, service accounts, and automated processes that facilitate machine-to-machine interactions. With the rapid proliferation of these identities, organizations must prepare for the unique challenges they present in terms of security and management.
Non-human identities are digital constructs that enable machines and applications to authenticate and interact with each other without human intervention. Unlike traditional human identities tied to individual users, NHIs operate autonomously, often performing critical tasks that support business operations. Examples of NHIs include:
The rise of NHIs has been driven by the increasing complexity of enterprise systems, particularly with the shift towards cloud computing and microservices architectures. As organizations automate processes and integrate third-party services, NHIs have outnumbered human identities by a staggering margin—estimates suggest a ratio of 10 to 50 times more NHIs than human users.
Despite their critical role in modern IT environments, NHIs often remain a blind spot in cybersecurity strategies. Traditional security measures designed for human identities—such as Multi-Factor Authentication (MFA) and regular password changes—are not applicable to NHIs. This lack of tailored security protocols creates significant vulnerabilities. For instance:
As cybercriminals become more sophisticated, they exploit these vulnerabilities. Attacks targeting NHIs can lead to unauthorized access, data breaches, and severe damage to organizational integrity.
The rise of Non-Human Identities (NHIs) marks a critical shift in organizational security. Recent studies indicate that over 80% of organizations have more NHIs than human users, with projections suggesting a ratio of 50 to 1 in the coming years. This growth highlights the urgent need for effective identity management practices. Poorly managed NHIs can lead to significant risks; for instance, 90% of successful cyberattacks exploit vulnerabilities associated with these identities. As businesses increasingly rely on automation and interconnected systems, securing NHIs is essential for protecting sensitive data and maintaining operational integrity.
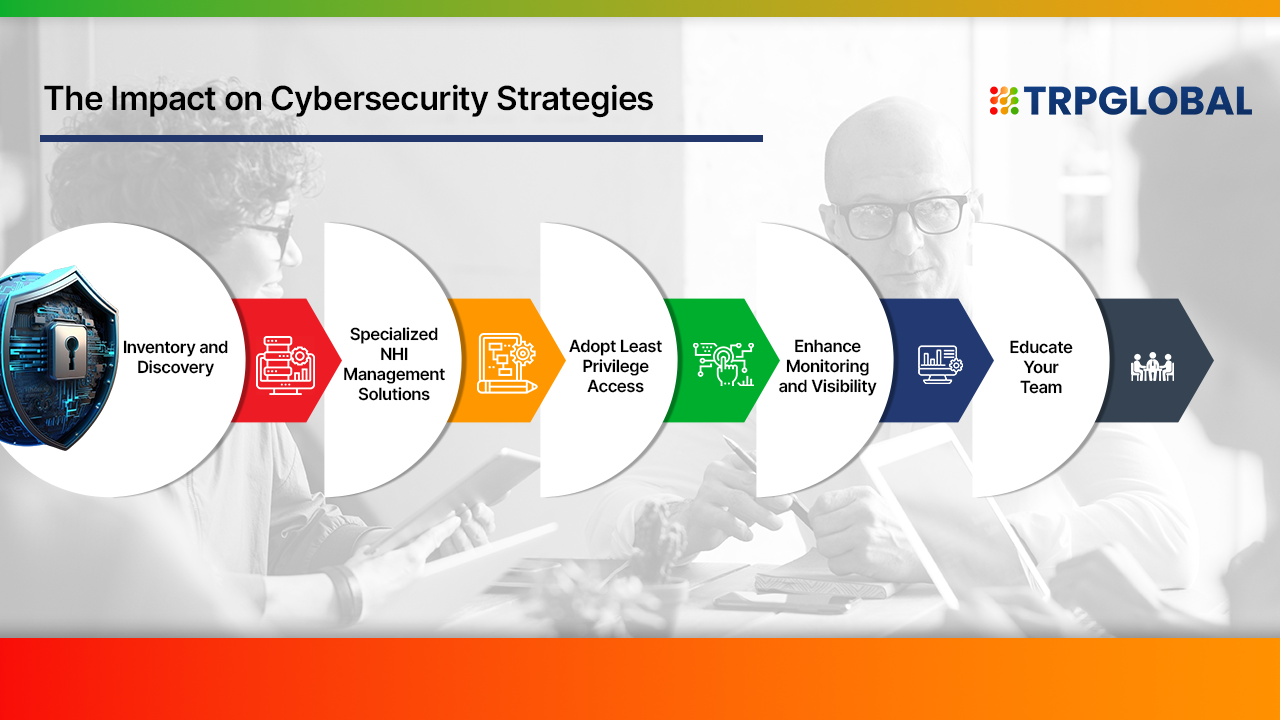
The rise of non-human identities necessitates a reevaluation of cybersecurity strategies. Here are some key considerations for organizations looking to enhance their security posture:
As we look towards 2025 and beyond, it is clear that non-human identities will continue to proliferate as organizations increasingly rely on automation and machine-to-machine interactions. To future-proof against potential threats posed by these identities:
The rise of Non-Human Identities presents both opportunities and challenges for organizations navigating the digital landscape. By recognizing their significance and implementing robust management practices tailored to these digital entities, businesses can mitigate risks and strengthen their overall security posture.
As we move forward into an increasingly automated future, addressing the complexities surrounding NHIs will be crucial in safeguarding organisational assets against cyber threats.
If you’re concerned about your organisation’s approach to managing Non-Human Identities or want assistance in implementing effective solutions, contact us today for a free assessment! Together, we can ensure your cybersecurity strategy is equipped for the challenges ahead.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.