Your SAP system isn’t just running your business it’s leaking the crown jewels if you’re not paying attention. For years, patching and credential hardening took center stage. But now, according to the latest SAPinsider–Onapsis research, data exfiltration has surged to the top as the most urgent threat targeting SAP systems. In this new era of digital transformation and cloud-enabled business models, outbound data is the new battleground.
This blog explores why data exfiltration has eclipsed traditional security concerns, how attackers are targeting modern SAP architectures, and what IT/security leaders must do to stay ahead of the curve.
Over 92% of survey respondents consider the data in their SAP systems to be “mission-critical or highly important”. From finance and supply chain data to HR records and pricing models, SAP is a goldmine for attackers looking to steal intellectual property, disrupt operations, or manipulate strategic outcomes.
Concerns about connections to other systems jumped from a tenth-place ranking last year to third in 2025. The rise of cloud, hybrid environments, and API-based integrations make SAP systems more interconnected—and, unfortunately, more vulnerable to exfiltration attacks.
Despite years of focus, patching remains the top challenge, with 35% of organizations citing downtime scheduling and patch validation as major blockers. Delayed patching opens windows for threat actors to exploit vulnerabilities and siphon data.
Unlike ransomware or service outages, data exfiltration doesn’t always trigger alarms. Attackers know this, which is why they increasingly use low-and-slow techniques to siphon sensitive data—financial records, customer data, or proprietary formulas over weeks or even months. In fact, SAP’s own advisory boards have highlighted that over 60% of recent insider-led incidents involved unauthorized data access rather than direct system manipulation. The stealth nature of these breaches means organizations may only discover the leak when regulators or customers raise red flags—far too late to contain the damage.
Traditional security controls aren’t enough for SAP landscapes because the platform spans business-critical applications, third-party integrations, and hybrid deployments. That complexity creates blind spots. Forward-thinking enterprises are adopting Zero Trust principles for SAP segmenting access at the role level, applying behavioral analytics, and monitoring data movement in real time. By treating every access request as potentially hostile, companies can shrink the attack surface and reduce the chance that a malicious insider or compromised account walks away with sensitive data undetected.

A devastating example emerged in early 2025: CVE-2025-31324, a zero-day vulnerability in SAP NetWeaver Visual Composer, allowed unauthenticated actors to upload malicious files resulting in remote code execution and full system compromise. Cybersecurity firms, including Palo Alto’s Unit 42, confirmed that attackers leveraged this flaw to deploy a stealthy Linux malware backdoor named Auto-Color, capable of reverse shells, file uploads, and hidden persistence.
In one dramatic instance, Darktrace detected exploitation activity six days before public disclosure, while CISA added the vulnerability to its Known Exploited Vulnerabilities Catalog.
This exploit illustrates the perfect exfiltration vector gain access through a vulnerability, execute commands, and quietly siphon data out via backdoors or chained payloads.
As organizations connect SAP systems with cloud services, BI tools, and legacy apps, misconfigured access and weak API governance become common paths for data leakage. Attackers increasingly run transient queries, mimic valid requests, and harvest data in small batches to evade logs.
Legacy SIEMs often miss SAP-specific attack patterns. Deploy extended detection solutions and ML-driven anomaly monitoring to flag unusual data exports or abnormal user behavior.
Case Study: From Attack Vector to Defense Strategy
A global manufacturing firm with sensitive trade-secret workflows falling under SAP data flow integrated anomaly detection across their SAP landscape. Within weeks, the system flagged irregular data pulls by a service account. Investigation revealed a supply chain breach symbiotically pulling strategic documents for future IP theft.
Quick action including forced reset of accounts, segmented data access, and accelerated patching prevented data loss. The firm embedded these defensive upgrades into their SAP risk strategy moving forward.
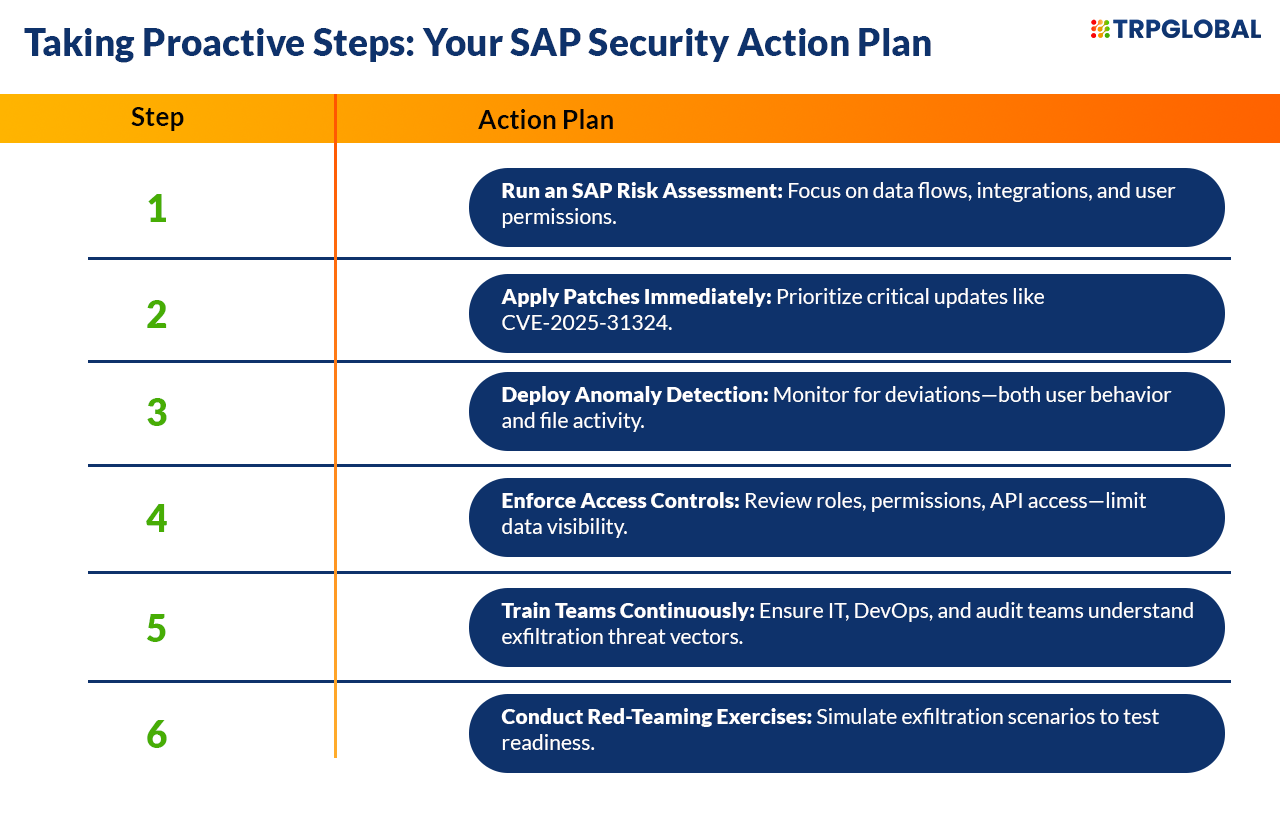
Is your SAP environment truly data-safe? Don’t wait for breach headlines to enforce change. Contact us now for SAP data risk mitigation, where we’ll walk you through live demos, response playbooks, and tools to help secure your systems from exfiltration threats.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.