The cloud has transformed the way enterprises build, scale, and secure their digital ecosystems. Yet, amid this transformation, one concept remains widely misunderstood: shared responsibility.
Every cloud provider from AWS to Azure and Google Cloud promotes the idea that security and compliance are “shared” between the provider and the customer. But in practice, this model often collapses under complexity. Cloud security incidents continue to rise, not because of technological failures, but because of governance gaps, unclear ownership, and broken accountability frameworks.
In 2025 and beyond, fixing shared responsibility isn’t just about defining who does what. It’s about rearchitecting accountability to align with real-world cloud operations, regulatory expectations, and continuous assurance.
When the shared responsibility model was first introduced, it was meant to simplify cloud security. Providers would secure the physical and virtual infrastructure, while customers would secure data, users, and configurations.
But today’s cloud isn’t simple. Hybrid and multi-cloud environments, thousands of APIs, microservices, and automated pipelines have blurred those once-clear boundaries.
The result? A dangerous accountability gap.
A recent IBM Cloud Threat Report found that 67% of cloud breaches stem from customer misconfigurations or role confusion, not provider flaws. That statistic alone proves the shared responsibility model, as currently implemented, is broken.
Traditional governance models were built for static, on-premise systems — not for dynamic cloud architectures. In those environments, accountability was tied to physical assets and clear departmental ownership.
Cloud computing changed that equation. Today:
The result is a fragmented accountability structure where no one owns end-to-end security, even though everyone assumes someone does.
To fix shared responsibility, organizations must shift from policy-based accountability to evidence-based accountability a governance model that continuously proves who is responsible, what they control, and how effectively that control operates.
This model transforms shared responsibility from a theoretical concept into a collaborative governance framework.
Instead of a static “provider vs. customer” view, accountability must now reflect the shared lifecycle of cloud operations design, deployment, monitoring, and assurance.
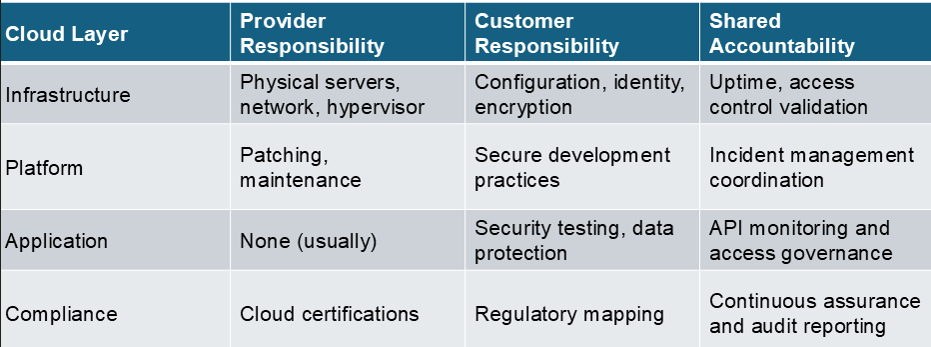
The message is clear: shared doesn’t mean equal. Each side must execute its role with precision and transparency.
How to Rebuild Cloud Governance for Shared Responsibility
The key to fixing shared responsibility lies in reengineering governance making it dynamic, automated, and integrated across your organization.
Document all cloud services and map out who owns what. Build a Responsibility Matrix (RACI) that covers:
This eliminates ambiguity and aligns operational control with compliance frameworks like NIST 800-53, CIS Benchmarks, and ISO 27001.
Governance shouldn’t live in a PDF document; it should live in your pipelines. Integrate policies into CI/CD so compliance and security checks occur automatically during deployments.
Use continuous control monitoring (CCM) tools to verify that configurations remain compliant. This ensures controls don’t drift between audits and enables real-time accountability.
Cross-functional collaboration is essential. Create a governance body including representatives from Security, IT, Risk, and DevOps to:
Accountability should be measurable. Track KPIs such as:
Metrics make accountability tangible, not theoretical.
Manual assurance can’t keep up with modern cloud velocity. AI-driven automation is reshaping governance by continuously monitoring risk, compliance, and performance.
Examples:
These technologies don’t replace accountability; they enforce it through transparency.
A global financial services company running workloads across AWS, Azure, and private cloud faced recurring audit findings about unclear control ownership. Each team thought another was responsible for cloud monitoring and incident escalation.
After a governance overhaul, the company implemented:
Within six months, audit exceptions dropped by 70%, and time-to-remediate fell by 40%. Shared responsibility finally became shared accountability.
Governance transformation isn’t just an internal initiative; it’s increasingly mandated by regulators.
Frameworks such as DORA (Digital Operational Resilience Act), NIS2, and SEC cyber disclosure rules now expect continuous visibility into cloud risks and control effectiveness.
This means periodic audits are no longer enough. Organizations must prove that their shared responsibility model is functioning — not just defined on paper.
Continuous accountability demonstrates to auditors, boards, and regulators that you can:
Ultimately, shared responsibility is about trust. Cloud providers and customers must share data, logs, and visibility to maintain that trust.
Transparency builds resilience. When providers expose telemetry data and customers share compliance status, both parties can respond faster to threats and prove control integrity to regulators.
This is the new model of partnership in cloud security: shared transparency, shared accountability, shared assurance.
By 2026, most leading organizations will adopt continuous assurance models, where accountability is validated in real time through AI, automation, and predictive analytics.
Cloud security governance will no longer depend on quarterly reviews but on continuous, event-driven evidence. The enterprises that master this shift will gain both regulatory confidence and operational resilience.
At TechRisk Partners (TRPGLOBAL), we help organizations design next-generation cloud governance frameworks that eliminate accountability confusion, automate compliance, and align with global regulations.
Our approach bridges security, IT, and compliance through actionable governance blueprints that make accountability measurable, visible, and enforceable.
If you’re ready to fix shared responsibility and future-proof your cloud security model, connect with us to start your governance transformation.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.