“Cyber resilience” is everywhere—on vendor slides, in boardroom decks, and baked into security strategies. But despite all the talk, most organizations still get blindsided by attacks that exploit old gaps, overlooked dependencies, or under-tested plans.
Because for too many companies, cyber resilience is a concept on paper—not a capability in practice.
And it shows. Look at the breaches and disruptions making headlines in the last 12 months. They weren’t all due to unknown zero-days or state-sponsored attacks. Many were the result of things like:
Let’s break down why “resilience” is falling short—and how to build something that actually works when it matters.
Cyber resilience isn’t just about preventing attacks. It’s about:
In simple terms: it’s your ability to take a hit—and keep moving.
That means going beyond perimeter security and looking at:
And more importantly, it means testing those assumptions under pressure—not just listing them in a policy document.
Tabletop exercises are valuable—but they’re not enough. If your incident response or continuity plans haven’t been simulated in a real-time, high-pressure environment, they’re unproven at best and dangerous at worst.
Many resilience strategies rely on ideal coordination between IT, legal, comms, and executive teams. In reality, roles blur, decisions stall, and finger-pointing starts once stress kicks in.
Most digital ecosystems are deeply interconnected. If your cloud vendor, payroll processor, or identity provider goes down, so do you. Resilience can’t stop at your firewall.
Threat actors evolve. Attack surfaces shift. Business priorities change. Resilience frameworks must be dynamic and continuously updated—not reviewed once a year during audit season.
In early 2024, a prominent healthcare technology provider suffered a ransomware attack that crippled systems for weeks. The impact wasn’t limited to the victim company:
The breach response was reactive. Business continuity plans existed—but hadn’t been tested against this type of supply chain disruption. The result? Operational chaos, reputational fallout, and millions in losses.
The Cost of Pretending You're Resilient
Research shows the average cost of a data breach in 2024 is $4.45 million, according to IBM’s latest report—and that doesn’t include lost contracts, delayed launches, or eroded customer trust.
Clients and partners expect transparency and control. If your first public statement comes 3 days after a breach, it’s already too late.
New data protection and critical infrastructure laws now require demonstrable resilience, including evidence of recovery plans, vendor risk controls, and crisis communications.
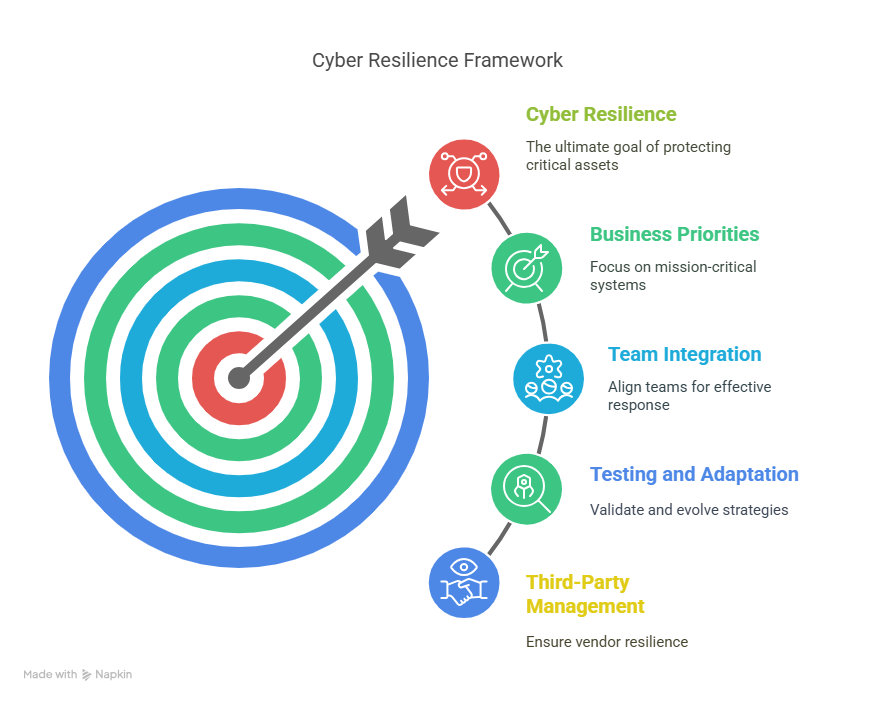
If you want more than a buzzword, you need a resilience framework that’s:
Not all systems matter equally. Identify what’s truly mission-critical and build layered protections and recovery plans around those assets.
IT, risk, legal, compliance, PR, operations—resilience only works when everyone is aligned. That means shared playbooks, joint simulations, and clear escalation paths.
Conduct not just tabletop exercises, but live-fire simulations, red team/blue team exercises, and scenario-based recoveries. Find the cracks before attackers do.
Your plan should evolve with the threat landscape and provide KPIs that leadership actually understands. Track recovery time objectives (RTO), incident response speed, and time to decision.
You’re only as resilient as your weakest link. Vet your vendors, review SLAs regularly, and ensure critical partners are included in continuity drills.
Here are a few diagnostic questions to ask yourself:
If your answers feel uncertain, your resilience is likely theoretical.
Buzzwords don’t stop breaches. Resilience isn't a slide in a strategy deck—it’s what kicks in when your controls fail, your inbox is flooded, and the media is calling.
You don’t get to claim resilience. You have to prove it—under stress, at speed, and in the spotlight.
Many organizations assume their MSPs, cloud providers, or cybersecurity vendors have resilience covered. But when the breach hits, it’s your systems, your data, your customers, and your leadership that take the hit. Resilience isn’t a line item—it’s a shared responsibility, and it must be intentionally embedded across architecture, operations, and governance. If your resilience depends entirely on third-party promises and passive policies, you’re not protected—you’re exposed.
We helps organizations move beyond the illusion of security into real, tested, measurable resilience. If you're ready to identify your blind spots, build a recovery-ready strategy, and avoid becoming the next headline, let’s talk.
Contact us and take the first step toward resilience that actually works.
In our newsletter, explore an array of projects that exemplify our commitment to excellence, innovation, and successful collaborations across industries.